Our Products
Monitoring and support
We utilize the leading in remote management software through VSA X (10) provided by Kaseya. This software simplifies management, reporting, and resolution of issues by reducing the time it takes to identify, address, and remediate issues across a host of platforms. It provides a single pane of glass for inventory, patching, server and network administration, reporting, discovery, and automatic addition of new devices.
Email security
We automate phishing and email security and is available both on Google Workspaces and Office 365. This platform enables clients to be secure in the knowledge that their user base is defended from malicious actors. As our system works for you, it evolves and learns to identify potentially malicious actors as well as suspicious email activity.
Phisiing testing and remediation
Otherwise known as ID agent, ID agent helps to run internal phishing email tests to users. This results in those who fail the test in getting remedial training, helping them maintain a high state of security awareness and enabling the organization to meet part of the high standard required for cyber security insurance. We can run these campaigns dynamically and automatically while offering instant reporting for awareness across the customer organization.
Full SOC (Security Operations center)
Customers who dont have massive teams in IT have often struggled with trying to attain the level of operational coverage needed for Cyber security. These teams are typically specialized and expensive to hire and its simply not feasible for small to medium size businesses. We answer that by providing a large set of automated and individually reviewed alerts. The system can flag incidents on the network for human review, at which point its referenced to their huge team of experts who help sort false positives from actionable information and pass that on to us to address the issues as they arise. We also enable compliance management and perform testing via tools like VulScan (Compare this to Nessus) as well as determining potential avenues for malicious actors to exploit.
Backup and disaster recovery
We take backups to the next level. Before, businesses were limited to taking bare metal backups that would have to be restored by a technician manually. Now, our operation allows rapid failover to a virtual version of the backed up machine either on premises or on the cloud to enable your business to experience absolutely minimal downtime. You can expect any system that is backed up to be available again in under an hour from the time the machine is reported to be down. The backup can then be used to restore the original machine to the desired state. Additionally, we offer file level backups as well so that no file will be lost.
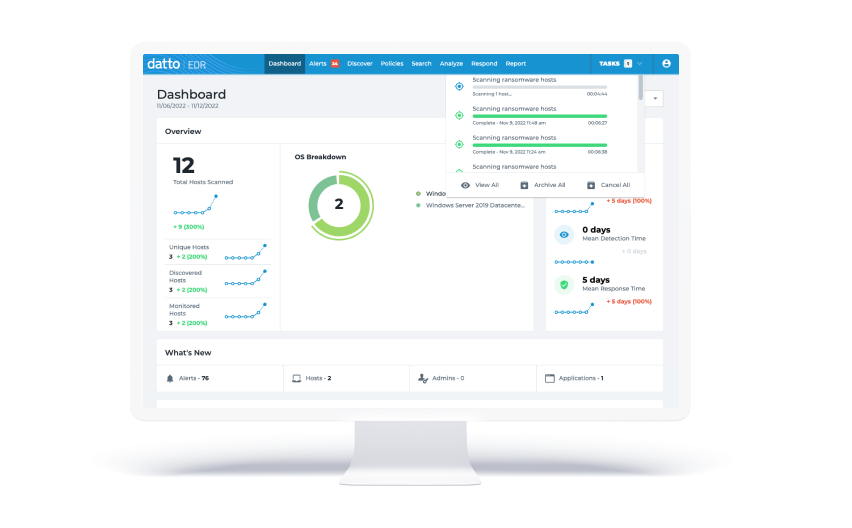
Endpoint detection and response
We provide a single pane of glass to monitor and respond to Anti Virus alerts and provides easy, rapid analysis to endpoint security issues in real time. This enables us to rapidly respond and head off issues before they occur. Using EDR gives us the ability to provide you with peace of mind, knowing that your devices are always protected with the latest updates for Anti Virus and letting us run scans on machines both on schedule and on demand.